Algorithms and Milkshakes
Created Tuesday 22 February 2022
FROM THIS

To THIS

(and back?)
Milkshake Model
(Incidentally)
Source Code -> Binary
Milkshake Model
DELIBERATELY
Encryption and Hashing.
Milkshake Model
Encryption - Hard to turn back

Milkshake Model
Hashing - *Impossible* to turn back, more later

Dan Brown
(wrote a dumb book)

Unbreakable Encryption Probably Still Exists
Yep, even given all the NSA stuff. You have to be super careful
(all breaking you see is usually "backdoors"
not fundamentals)
Encryption
The basic tools for encryption are mostly available to all…
...even if the social factors, companies, corporations, and governments aren’t down.
(remember, you gotta have it on BOTH SIDES)
Old School Encryption
Caesar Cipher. (yes, this really used to fool people)
DWWDFN WKH HDVW ZLQJ RI WKH IRUW DW WKUHH RQ WKXUVGDB..
you got it
attack the east wing of the fort at three on thursday
Quick aside: Another thing
What about hiding the message ITSELF?
Shave a guy's head ... and wait?
Steganography
Hiding the fact that the message (or payload) exists at all
Examples:
- fake personal ad to say something else
- having a safe but hiding valuables in a shoebox
- weird bits in a jpg
History of Hidden Messages
- Navajo Code Talkers
- “Tactical” Negro Spirituals
Languages, dialects, patois'...
CULTURAL ENCRYPTION.
CULTURAL AUTONOMY.
(ever heard of “code switching?”)
Recap
Steganography v. Encryption
Steganography
- Hiding the fact that the message/payload exists at all; e.g.
- fake personal ad to say something else
- having a safe but hiding valuables in a shoebox
- weird bits in a jpg
Steganography
Useful, but imperfect, esp online
Bad, because: Robots and radio

Better..
Why YES, you can have a copy.
OF JUNK! TOO BAD YOU CANT READ IT!
(This is Encryption)
Encryption: Sending VERIFIABLE secrets
ALICE needs to send a verifiable message to BOB
but CAROL is trying to listen in.
“This is a conversation between A and B so you can C your way out!”
Some definitions:
CLEARTEXT - (should be obvious)
CIPHER - The system of encryption
CIPHERTEXT - the (hopefully not-understandable) gibberish generated
KEY - the arbitrary decoding or encoding "key/password-ish thing" - sometimes not both.
More strategy
Secret METHOD
vs
Public METHOD, secret KEY
Why not interrogate the creators?
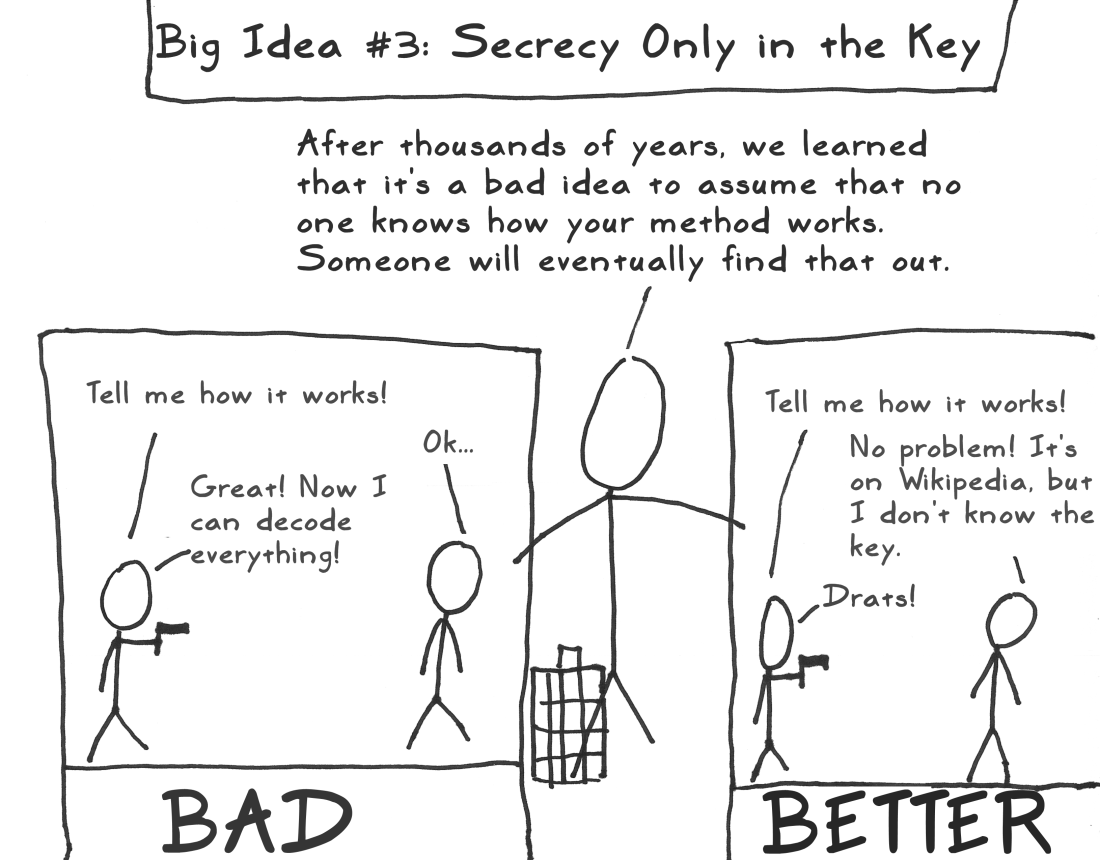
Some standard ideas
Security through obscurity* is generally a bad idea:
*The STRICT definition, meaning
"Relying on secrecy in implementation or design,
NOT in the key"
Security through obscurity
"Any person can invent a security system so clever that she or he can't think of how to break it."
Schneier's Law
(you can generalize this to a lot of things; e.g. Open Source, Auditing, etc)
Never roll your own
(Or better yet, do, and throw it out. You'll learn something)
Better
New Strategy, if you can meet
The bookstore strategy
OR
The One-Time Pad
but what if you CAN'T meet each other...
But, we are usually "strangers"
- Public (asymmetric) Key Encryption
- Diffie Hellman Key Exchange.
Whats Mathy and Milkshakey?
What, even for a computer, is VERY FAST in one direction..
..and IMPOSSIBLY SLOW in the other?
(remembering,
all computers do is math?
Hey, remember factoring?
24
4 * 6
2 * 2 * 2 *3?
What about 17?
What about 17?
PRIME
It's MATH all the way down
One Way Strategies.
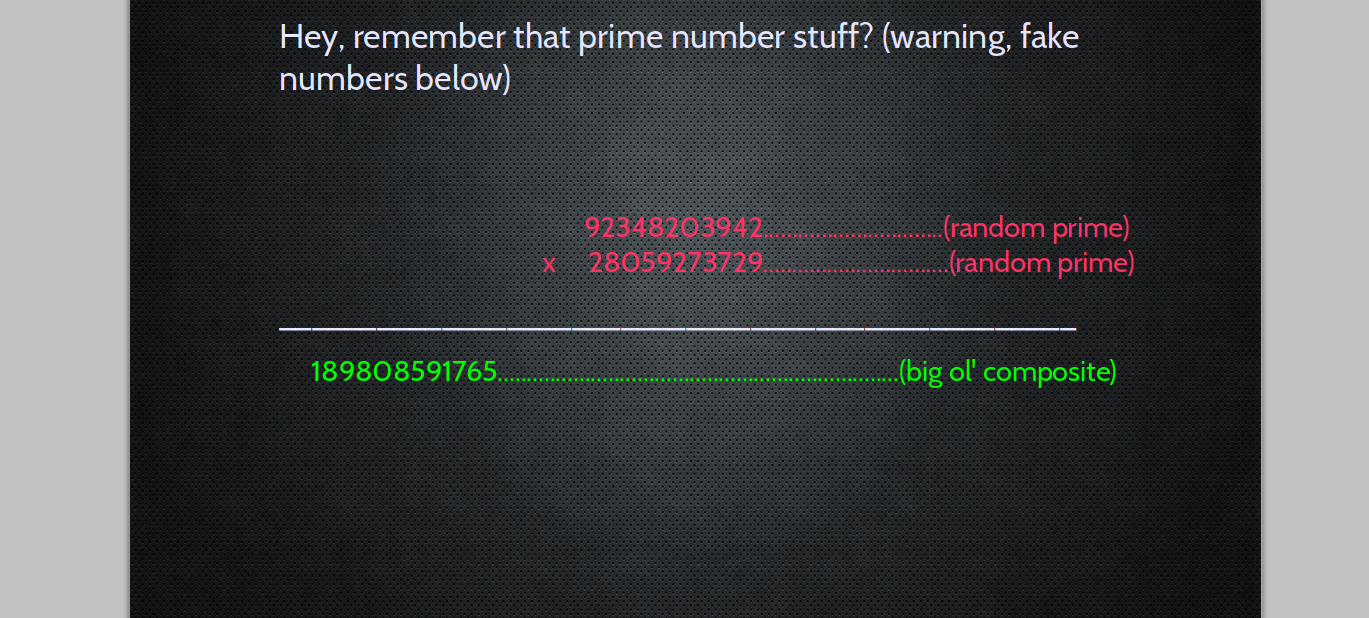
So we use this for KEY encryption
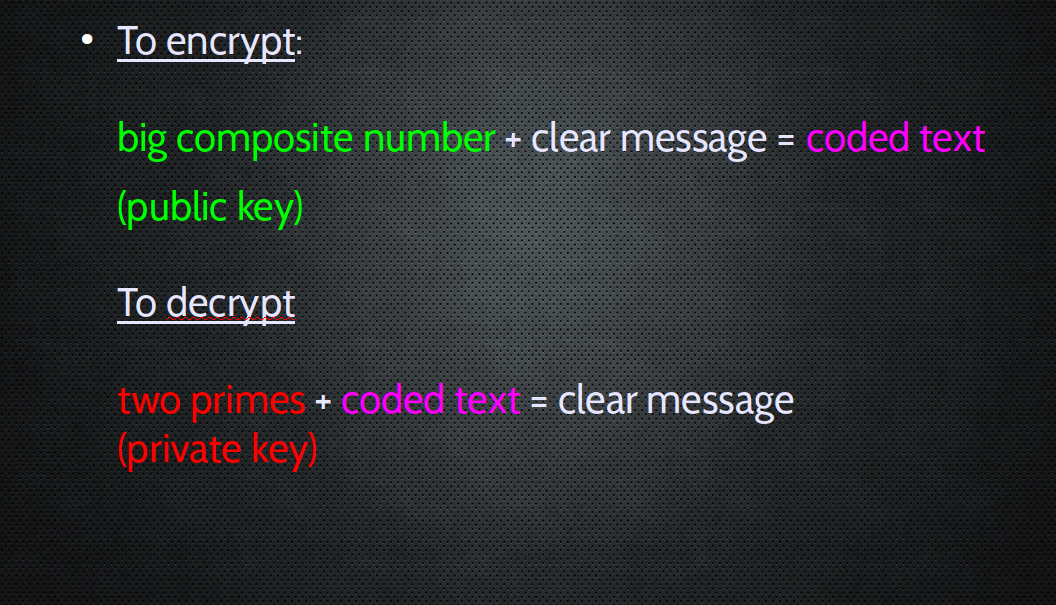
Phil Zimmerman
Invents this. "Hey, this is pretty good privacy!"

Eben Moglen
"Cool idea, no cap. Also, when the FBI kicks down your door, holla"

One weird flipside of this:
Who's MORE powerful than the government?

Gotta sign checks and credit cards!
Encryption and Signatures
Encryption and digital signatures are two sides of the same coin.
You need digital signatures to send money, so we also have encryption. (mostly)
Let's slow down because this is amazing
Because wait: If it's just me and you, its like we just met.
But if it's
Amazon ,Buyer and Card thief..?
and we want to keep this on going.
No seriously. Remember my "mesh" from before?
If ALL THE SIGNALS ARE IN THE AIR
and MY COMPUTER or PHONE HAS TO SEE ALL OF THEM
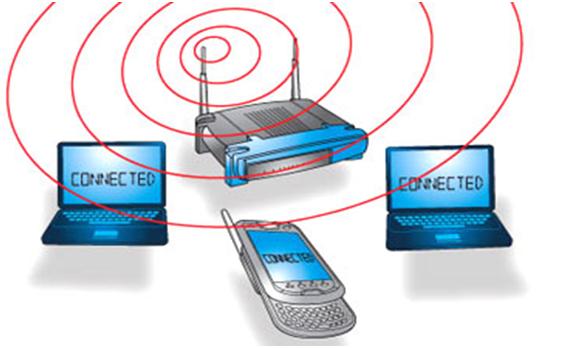
Why can't I just steal the password the first time you send it?
What if I do this dirtiness
I invite you to my house,
where I have COMPLETE CONTROL of my router.
I get you to buy something from Amazon for the first time ever
HOW DO I NOT STEAL YOUR CREDIT CARD?
I'm watching LITERALLY ALL OF THE TRAFFIC?
DIFFIE HELLMAN
(pretend that you can't "unmix" colors. Milkshake)
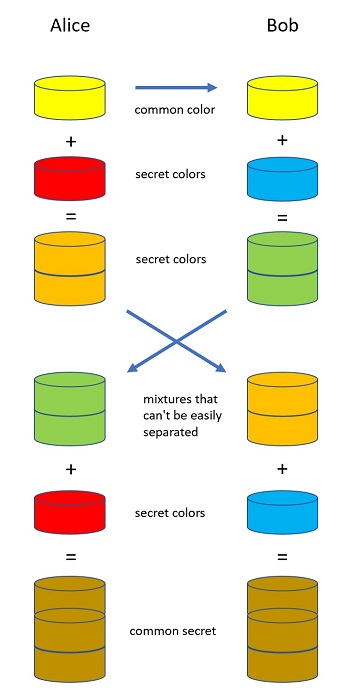
Also — Passwords
When you lose your password, what does the website do?
Make you change it?
Or
Send you a copy of it.
If they're nice enough to send you your password?
If they're nice enough to send you your password?
THEY SUCK AT SECURITY.
Good websites will NOT send you your password.
Because they don't actually know it.

Encrypted passwords, right?
...kinda.
One way to do this:
1) Get their password
2) Save it on your computer
3) Then, encrypt it for safety.
What do we really need?
The actual password
or
simply:
Proof that they typed in the same thing both times?
What do we really need?
Remember: “encrypting” something always yields:
GIBBERISH
“MyPassword123” > ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab
What do we really need?
Remember: “encrypting” something always yields:
UNIQUE GIBBERISH
“MyPassword123” > ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab
means that
”DifferentPassword456” ≠ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab
So NEVER save the password,
just the gibberish!
NOT
“MyPassword123” = “MyPassword123”
BUT
“ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab”
=
“ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab”?
And “MyPassword123” IS NOT ON THE SERVER
Wait, do we need alladis?
“ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab”
=
“ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab”?
Try this
“ab18db351a3”= “ab18db351a3”*
As long as
we use ALL the data in the original to get this number
And it’s STILL mathematically unliklely that two different passwords will yield the same short gibberish, we’re good to go.
(not exactly this)
A dumber, similar thing
Presumption: The network (or person) is imperfect. The bytes we receive may not always be the exact ones that were sent.
Also: The network or verification is “slow”
We need a shorter, but verifiable, version of the data.
Hashing
Error checking/Checksumming.
One tiny change in the original still means BIG changes in the gibberish.
(MD5, which is fast, but not super-secure) is good for this)
Hashing
Error Checking/Checksums
Password “Storage”
Bitcoin/Cryptocurrencies
Passwords
They don't store your password (your secret ingredient)
They just store the entire milkshake....and calculate/mix it every time.
(don't use MD5, use something deliberately slow, like bcrypt)
To beat up some more analogies
Consider your mom’s _______ recipe?
(milkshake?)
Even if you don’t know the ingredients..
… you know when it’s WRONG :)
More details on Hashing
Horrible – storing the password
Better but still bad – storing the password hashed
Decent – storing “userid+password” hashed
Best – storing “userid+password+salt” hashed
Process
Login: jmarks
password: g00dpassword
(salt): b00gab00ga
jmarks+g00dpassword+b00gab00ga
==HASHED==>
02f39aae85ad73e162b446e918597e89
Practical Matters
RANDOMNESS
Pseudo-randomness is easy:
"Multiply big'ol numbers a bunch and chop off the beginning of them"
TRUE Randomness is surprisingly hard
RANDOMNESS
In a sense, you can't do it "inside" the computer.
Cloudflare

Is Cybersecurity THAT bad today?
imho, yes.
This engineering v?

This

I do blame this guy

The ultimate office APPLIANCE
Missed it
"Sometimes we do get taken by surprise. For example, when the Internet came along, we had it as a fifth or sixth priority." - Bill Gates
And so
Bad ideas like
autorun.inf
aka
Lack of "Permissions"
If I handed you a piece of paper that said
"Go jump off a bridge?"
To say nothing of misleading language
"Virus"
Backdoors
Yep, they're going to KEEP TRYING THIS MESS.

PRACTICAL MATTERS
DON'T ROLL YOUR OWN...better yet
PRACTICAL MATTERS
DEMAND only free and open source here, confirmed by e.g. NIST
Anything else is almost CERTAINLY compromised in real life.
PRACTICAL MATTERS
All software is imperfect and may have bugs;
..watch out as they may try to use this against you.
PRACTICAL MATTERS
Don't fall for the "Security through Obscurity" trap
(as in, actually reinforce, don't just hide)

PRACTICAL MATTERS
- OR for the "Security through Obscurity trap" trap
(additional hiding to reinforcement isn't bad, aka someone might seriously say, DONT PAINT THIS CAMO.)

Rubber Hose Decryption
Watch the endpoints, this is where the vulnerabilities are
Finally - encrypted AGAINST WHOM?
You'll have to do a fair bit of "game theoretical" thinking here,
when you're dealing with "black-box" encryption.
E.g. Whatsapp claims to be end-to-end encrypted?
I legit don't know.
Third Party Password Managers?
"Three people can keep a secret if two of them are dead?"
How to be a Cybersecurity Expert..
without knowing any technology at all?
How to be a Cybersecurity Expert..
without knowing any technology at all?
"Skin in the game," easy.
This guy....
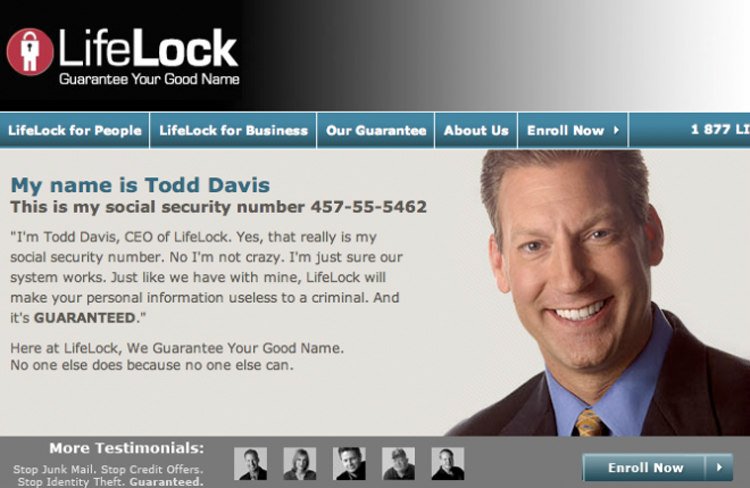
So what then?
SKIN IN THE GAME
Shift the risk to the responsible party.
That's the tweet.
Hammurabi's Code
If a builder builds a house for a man and does not make its construction firm, and the house which he has built collapses and causes the death of the owner of the house, that builder shall be put to death.
SO THEN
When some smug sales rep from TechnoSafeCo shows up at your organization:
We use the latest 256-bit SSL encrypted zippity zorp doobie doo
to fragulate your mainframes flux capacitor for 99.9% reliability!
SO THEN
You raise your hand and say 99.9%? GREAT!
Our data and relationships are worth a million dollars. We'll pay you $1000 a month...
...if YOU INDEMNIFY US IN CASE OF A BREACH.
i.e., we get breached, you pay us a million*
SO THEN
*Again, this will either save your company or get you fired for saying it out loud.
GOOD LUCK!
(shout out to the hero Todd Davis)