Privacy, Verification, Incentives
Created Tuesday 04 June 2024
Week 5 - Encryption

Sending VERIFIABLE secrets
ALICE needs to send a verifiable message to BOB but CAROL is trying to listen in.
Some definitions:
CLEARTEXT - (should be obvious)
CIPHER - The system of encryption
CIPHERTEXT - the (hopefully not-understandable) gibberish generated
KEY - the arbitrary DECODING or ENCODING "thing/data/password-ish thing" - sometimes not both.
Steganography
- Hiding the fact that the message/payload exists at all; e.g.
- fake personal ad to say something else
- having a safe but hiding valuables in a shoebox
- weird bits in a jpg
Steganography is less preferred..
..when your attacker can potentially "see" everything.
EG, the internet, or even...

Some standard ideas
Security through obscurity* is generally a bad idea:
*The STRICT definition, meaning
"Relying on secrecy in implementation or design,
NOT in the key"
Security through obscurity
"Any person can invent a security system so clever that she or he can't think of how to break it."
Schneier's Law
(you can generalize this to a lot of things; e.g. Open Source, Auditing, etc)
Never roll your own
(Or better yet, do, and throw it out. You'll learn something)
Better
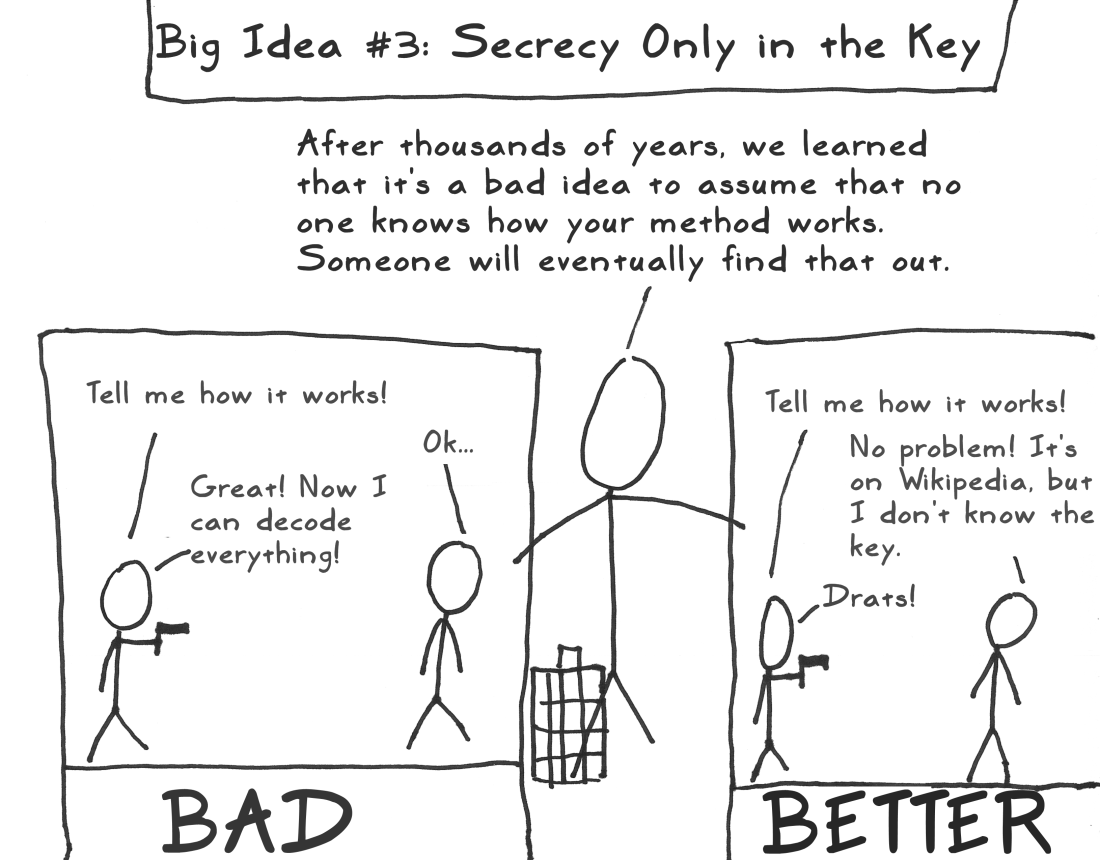
Quick note on "Security Through Obscurity"
Sometimes people use this as an equivalent to Steganography, though not quite.
I.E the great
"Should you change your SSH Port" Debate?"
What's the answer?
Against a determined attacker trying to get you personally? No point.
But, as the joke goes, it won't make you faster than the bear, but it will
make you faster than the other hunter.
It's MATH all the way down
One Way Strategies.
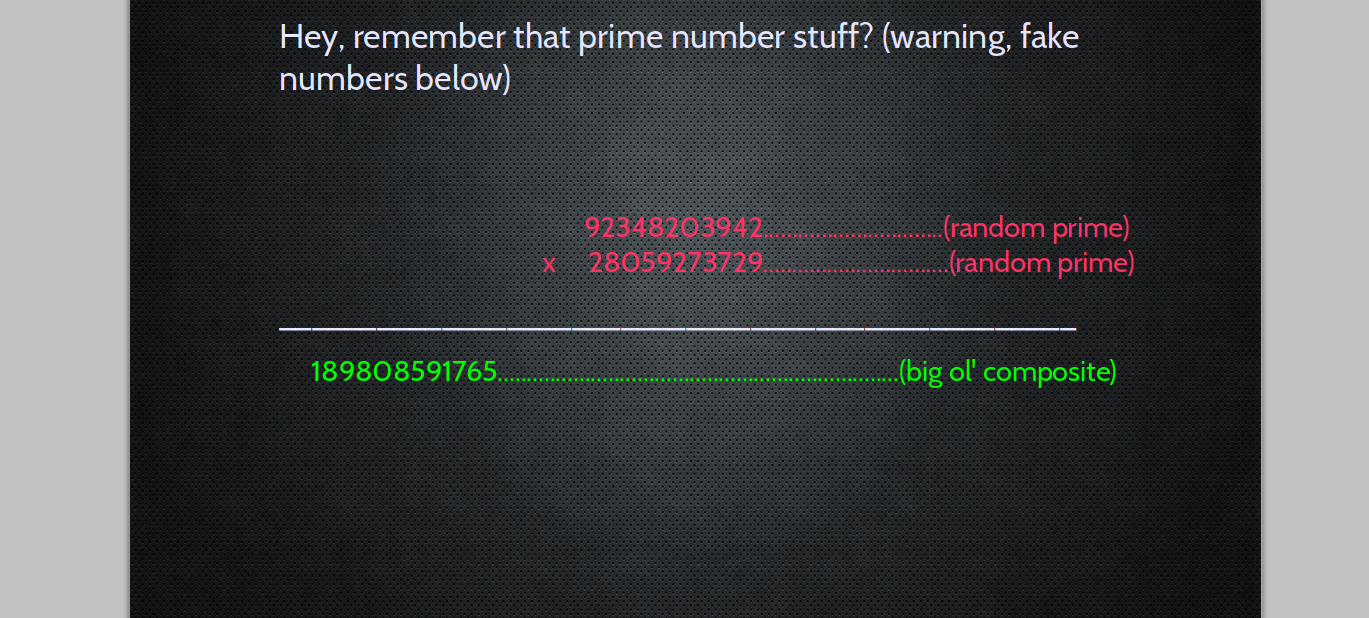
Really, it's KEY exchange that's a big deal
If you and your conspirator can "meet" - this makes things easy:
- Bookstore Strategy
or better yet
- One Time Pad
(Note that OAuth 2FA is *a lot* like this, but not identical. The overriding 2FA code is like the "book")
But, we are usually "strangers"
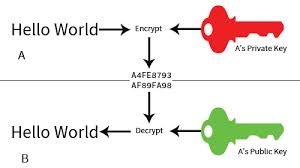
Enter PUBLIC KEY ENCRYPTION
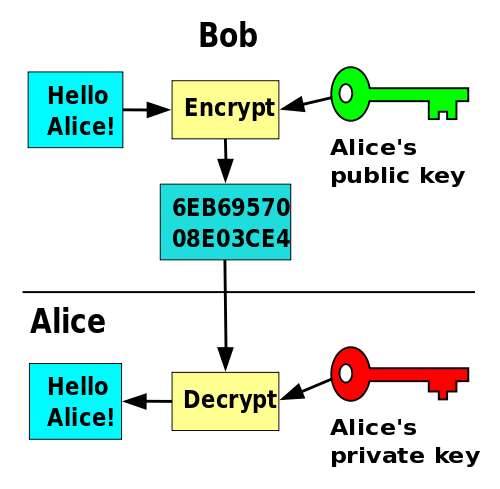
So we use this for KEY encryption
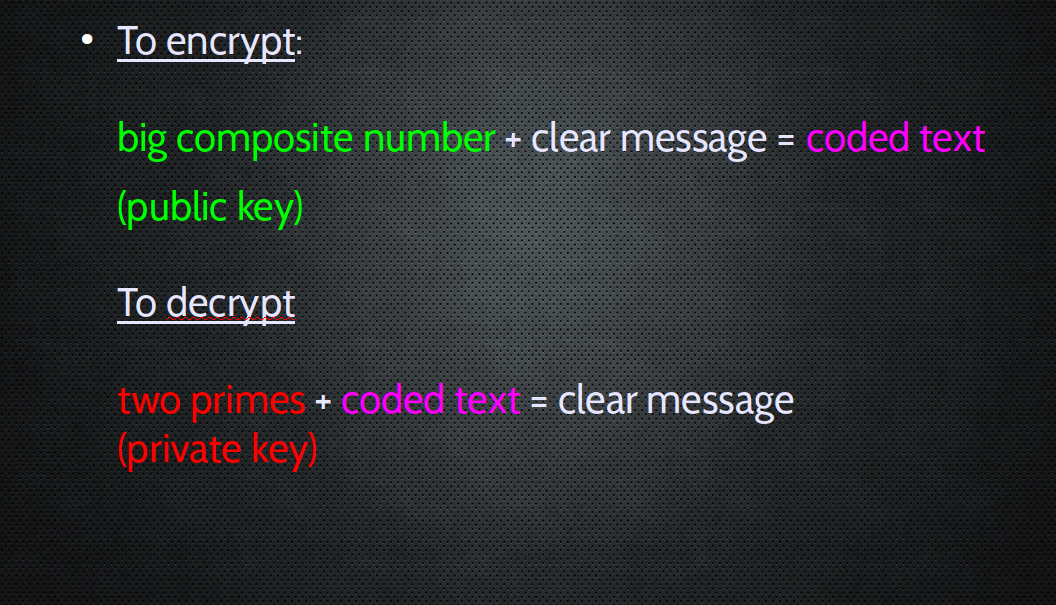
The weird flipside of this:
SIGNATURES
IMPORTANT PRACTICAL PRINCPLES
RANDOMNESS
Pseudo-randomness is easy:
"Multiply big'ol numbers a bunch and chop off the beginning of them"
TRUE Randomness is surprisingly hard
RANDOMNESS
In a sense, you can't do it "inside" the computer.
Cloudflare

Backdoors
Yep, they're going to KEEP TRYING THIS MESS.

PRACTICAL MATTERS
DON'T ROLL YOUR OWN...better yet
PRACTICAL MATTERS
DEMAND only free and open source here, confirmed by e.g. NIST
Anything else is almost CERTAINLY compromised in real life.
PRACTICAL MATTERS
All software is imperfect and may have bugs;
..watch out as they may try to use this against you.
PRACTICAL MATTERS
Don't fall for the "Security through Obscurity" trap
(as in, actually reinforce, don't just hide)

PRACTICAL MATTERS
- OR for the "Security through Obscurity trap" trap
(additional hiding to reinforcement isn't bad, aka someone might seriously say, DONT PAINT THIS CAMO.)

Rubber Hose Decryption
Watch the endpoints, this is where the vulnerabilities are
Finally - encrypted AGAINST WHOM?
You'll have to do a fair bit of "game theoretical" thinking here,
when you're dealing with "black-box" encryption.
E.g. Whatsapp claims to be end-to-end encrypted?
I legit don't know.
Week 6 - Passwords and Hashing
Created Monday 28 September 2020
Passwords
When you lose your password, what does the website do?
Make you change it?
Or
Send you a copy of it.
If they're nice enough to send you your password,
you can rest assured..
If they're nice enough to send you your password,
you can rest assured..
that they suck at security.
Good websites CANT send you your password.
Because they don't actually know it.
HOW?
Obviously, if you're storing passwords, you want them "encrypted"
One way to do this:
1) Get their password
2) Save it on your computer
3) Then, encrypt it for safety.
but wait
What do we REALLY need?
The actual password
or
simply:
Proof that they typed in the same thing both times?
What do we REALLY need?
Remember: "encrypting" something always yields:
GIBBERISH that MUST BE
UNIQUE
"MyPassword123" > ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab
So, let's just switch it:
ANOTHER way to do this: ON FIRST LOGIN
1) Get their password
2) ENCRYPT IT FIRST for safety.
3) Then save the ENCRYPTED password.
So, let's just switch it:
ON NEXT LOGIN
1) Get password
2) Encrypt it the same way, then compare the gibberish!
SO NOT
"MyPassword123" = "MyPassword123"
but instead..
"ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab"
=
"ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab"?
And "MyPassword123" IS NOT ON THE SERVER
But wait: Let's do one more thing?
Do we really need all of this?
"ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab"
=
"ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab"?
But wait: Let's do one more thing?
What about just:
"ab18db351a3"= "ab18db351a3"*
As long as
we use ALL the data in the original to get this number
And it's STILL mathematically unliklely that two different passwords will yield the same short gibberish, we're good to go.
*you don't quite just cut a chunk off, but it's like this
But wait: Let's do one more thing?
Do we really need all of this?
"ab18db351a3"= "ab18db351a3"*
ADVANTAGES:
It's shorter
Now you LITERALLY CANNOT "decrypt" it because you're missing some information. This is good!
And, now - we can use this verification method on things other than passwords as well.
Hashing
"Used to map data of arbitrary (big) size,
to (non-informative) data of fixed (small) size."
To Illustrate, first something slightly dumber...
File Verification
Presumption: The network (or person) is imperfect. The bytes we receive may not always be the exact ones that were sent.
Also: The network or verification is "slow"
We need a shorter, but verifiable, version of the data.
Basic Checksumming
(technically the following is NOT checksumming)
Basic Checksumming
The grocery list:
Cheese
Crackers
Eggs
Ham
Koala
Mangoes
Salt
Underwear
Send the following...
Cheese
Ham
Eggs
Crackers
Koala
Salt
Underwear
Mangoes
CHECKSUM.45
CHECKSUM.45 = CHECKSUM.45
If the reciever gets
Cheese
Ham
Eggs
Crackers
Salt
Underwear
Mangoes
CHECKSUM.45
CHECSUM.40 = CHECKSUM.45? NO, SEND AGAIN.
Hashing
Error checking/Checksumming.
One tiny change in the original still means BIG changes in the gibberish.
(MD5, which is fast, but not super-secure) is good for this)
Verification:
Hashing Uses
Error Checking/Checksums
Password "Storage"
Bitcoin/Cryptocurrencies
Passwords
They don't store your password
(your secret ingredient)
They just store the entire milkshake....and calculate/mix it every time.
(don't use MD5, use something deliberately slow, like bcrypt)
To abuse some more analogies..
Consider your mom's _______ recipe?
(milkshake?)
Even if you don't know the ingredients..
... you know when it's WRONG :)
How passwords are done
Horrible - storing the password
Better but still bad - storing the password hashed
Decent - storing "userid+password" hashed
Best - storing "userid+password+salt" hashed
For example
Login: jmarks
password: g00dpassword
(salt): b00gab00ga (or better yet, change it every time)
jmarks+g00dpassword+b00gab00ga
==HASHED==>
02f39aae85ad73e162b446e918597e89
Real life
Is Cybersecurity THAT bad today?
imho, yes.
This engineering v?

This

Sigh, passwords for humans
In the beginning, there was leetspeak
or should I say 1337sp34k.
n00b pr0n lololol
Hey, why did this happen in the first place? Not for passwords...
1337sp34k
We do this now, except we say things like "unalived" and "PDF file"
Warning: Controversy ahead.
I'm following NIST, what they say makes A LOT OF SENSE to me:
You WILL see disagreement, feel free to form your own opinion
The Good Idea
Allow for, and perhaps require LENGTH.
That's IT.
Think passPHRASES, not words
The Good Idea

Bad ideas
Composition rules:
"At least one upper and one lowercase and a number.."
(We have a better solution, which is length)
Bad ideas
Password rotation - i.e. Change passwords every:
NAH, just pick a good one in the first place
Bad ideas
Password hints and Security Questions aka
Knowledge Based Authentication
ALWAYS LIE ON THESE. THEY ARE JUST SECONDARY PASSWORDS
https://www.mcsweeneys.net/articles/nihilistic-password-security-questions

Not NIST, but what I recommend
Make a good password
Write them down on paper and put in your wallet or purse. (Schneier agrees)
If you think you gangsta like I do
Remember the encryption thing you just did?
I write down my passwords in an encrypted text file. That's it.
Password Managers?
teach the controversy I guess.
They make NO SENSE to me, but clearly some find them acceptable.
2fa - Two Factor Authentication
Usually, a password and .. something else
Something else?
SMS?
Email?
Authenticator?
Hardware?
SMS
Not bad, but proving to be grimy, because cell phone companies aren't good at this..
Also not bad, but it's like the default backup for everything, so there you go.
Authenticators
e.g. Oauth. Pretty good. One time passwords, very similar to the "Bookstore Method"
PS, YEP, I STORE MY OAUTH KEYS in that same file and generate my 2fa #s from the command line. WHAT.
FIDO - Hardware
I mean, I suppose.
Other ideas, again:
(prof's opinion)
Biometrics are stupid*
Other ideas, again:
Biometrics are as stupid as Social security numbers
(i.e. decent USERNAMES or slight SECURITY THROUGH OBSCURITY)
I don't use 'em.
A Warning:
Practicing what we discuss today can just as easily
get you fired as get you promoted.
Though we don't touch computers today, I'd
guess that today's is potentially the most hazardous to your career.
A bold idea:
You might be able to be really good at cybersecurity without knowing anything about computers.
This guy....
So what then?
SKIN IN THE GAME
Shift the risk to the responsible party.
That's the tweet.
Hammurabi's Code
If a builder builds a house for a man and does not make its construction firm, and the house which he has built collapses and causes the death of the owner of the house, that builder shall be put to death.
Whoa.
Grimy, I know:
The idea being: This sort of system sets up better incentives than the ones that came before.
Lots of milder examples:
Dogfooding:
The people who made Discord use Discord.
versus
When Yahoo Mail was a thing, more people were using Gmail.
MY DOMAIN AND EMAIL at jrm4.com
I pay 5 bucks a month for jrm4.com email and hosting.
This is very much more expensive than free, but....
MY DOMAIN AND EMAIL at jrm4.com
I can call and chat and yell at people if I have to, because HOSTDIMES reputation is on the line.
And so, true story, what if your dad manages to inexplicably delete all his email?
They said, we can fix this, but it will cost you.
MY DOMAIN AND EMAIL at jrm4.com
I can call and chat and yell at people if I have to, because HOSTDIMES reputation is on the line.
And so, true story, what if your dad manages to inexplicably delete all his email?
They said, we can fix this, but it will cost you FIFTEEN DOLLARS!!!
SO THEN
When some smug sales rep from TechnoSafeCo shows up at your organization:
We use the latest 256-bit SSL encrypted zippity zorp doobie doo
to fragulate your mainframes flux capacitor for 99.9% reliability!
SO THEN
You raise your hand and say 99.9%? GREAT!
Our data and relationships are worth a million dollars. We'll pay you $1000 a month...
...if YOU INDEMNIFY US IN CASE OF A BREACH.
i.e., we get breached, you pay us a million*
Risk Calculation
If 100 houses are each worth $100,000
and 1 house burns down every year
Then a reasonable insurance premium would be $1000 per homeowner...
..which goes to paying for the one house that burns down every year.
Switch out some words
If 100 cyber companies are each worth $100,000
and 1 is hacked out of existence every year
Then a reasonable insurance premium would be $1000 per company...
..which goes to paying for the one company that burns down every year.
SO THEN
Fairly certain LITERALLY NO TECH COMPANY
DOES THIS.
SO THEN
*Again, this will either save your company or get you fired for saying it out loud.
GOOD LUCK!
(shout out to the hero Todd Davis)
External Incentives (presently weak or nonexistent)
Regulation
Liability (Tort Law)
Contract
Time permitting...
Hey, so hashing again?
Hey, so these hashes
They look like--
02f39aae85ad73e162b446e9
What are the odds that it would look like, say..
00000ae85ad73e162b446e9
Not IMPOSSIBLE, just VERY UNLIKELY.
A bit on banks and money
What is most money "made of?" How is it stored? Coins and little green pieces of paper?
A bit on banks and money
What is most money "made of?" How is it stored? Coins and little green pieces of paper?
NOPE.
Just (trusted) lists. Ledgers in banks and such.
Usually "digital"
In fact, lists are older than "money" itself.
Not dollars, but a list somewhere that says
"Ug owes Oof two cows"
"Oof owes Grok a stick"
or more accurately
"everybody owes the king taxes"
theorem: any system that involves writing down "ownership" and "what you've paid" for is (possibly) a bank = (gamestop, even)
But, you also might want "pieces/tokens"
GOLD AND DIAMONDS HA HA HA
(wait, seriously. Why are diamonds more expensive than water?)
Bitcoin and most other "Cryptocurrencies"
(note, some others don't work exactly this way)
A huge encoded/distributed online ledger/list, also called a "blockchain"
Powered/driven by "mining" (which is more like a slot machine, pull the lever, power the thing, and see if you "win")
Mining Bitcoin?
Randomly trying to find "nice looking" hashes.
......4E9BB99 nope.
.......000000 yep! $$$$
Mining
When you download a bitcoin (full node) wallet program, you literally have to get a copy of every single transaction ever.
Transactions are computationally expensive.
The "Mining" also powers the "hashed transactions..eg."
02b23 gave bf239 .005 bitcoins. I can prove it because the hash of this transaction is =>
081ee23
Add this to the chain and spread it around.
Bitcoin transaction.
You "add your new or old hash movement" to the ledger. By making another special hash. Which is "expensive."
This work powers the blockchain and "proves" that you've put in work. By design, the system "rewards" you for it.
Bitcoin transaction.
Now, why is it valuable?
Because people believe it is.
See also: gold, beanie babies, crappy companies, virtual swords, pokemon cards, sneakers, whatevs.
Bitcoin transaction.
PS: Crypto addresses? Just numbers in different bases (sometimes with a prefix):
Functionally similar to public keys
ETH/PLS: 0x19C653CB3D30EeEe2F99f9f4B987E3b22880FFCF
(this is 100% real, please feel free to send me money :) )
"Blockchain"
It's a large public database, in which everyone can see every transaction. That's all.
Now give me a bunch of money because I just said "blockchain" :)