Week 6 - Passwords and Hashing
Created Monday 28 September 2020
Passwords
When you lose your password, what does the website do?
Make you change it?
Or
Send you a copy of it.
If they're nice enough to send you your password,
you can rest assured..
If they're nice enough to send you your password,
you can rest assured..
that they suck at security.
Good websites CANT send you your password.
Because they don't actually know it.
HOW?
Obviously, if you're storing passwords, you want them "encrypted"
One way to do this:
1) Get their password
2) Save it on your computer
3) Then, encrypt it for safety.
but wait
What do we REALLY need?
The actual password
or
simply:
Proof that they typed in the same thing both times?
What do we REALLY need?
Remember: "encrypting" something always yields:
GIBBERISH that MUST BE
UNIQUE
"MyPassword123" > ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab
So, let's just switch it:
ANOTHER way to do this: ON FIRST LOGIN
1) Get their password
2) ENCRYPT IT FIRST for safety.
3) Then save the ENCRYPTED password.
So, let's just switch it:
ON NEXT LOGIN
1) Get password
2) Encrypt it the same way, then compare the gibberish!
SO NOT
"MyPassword123" = "MyPassword123"
but instead..
"ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab"
=
"ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab"?
And "MyPassword123" IS NOT ON THE SERVER
But wait: Let's do one more thing?
Do we really need all of this?
"ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab"
=
"ab18db351a3ed3849cca9839d98381ee6392eeb391baa39d766290082812d9eceab"?
But wait: Let's do one more thing?
What about just:
"ab18db351a3"= "ab18db351a3"*
As long as
we use ALL the data in the original to get this number
And it's STILL mathematically unliklely that two different passwords will yield the same short gibberish, we're good to go.
*you don't quite just cut a chunk off, but it's like this
But wait: Let's do one more thing?
Do we really need all of this?
"ab18db351a3"= "ab18db351a3"*
ADVANTAGES:
It's shorter
Now you LITERALLY CANNOT "decrypt" it because you're missing some information. This is good!
And, now - we can use this verification method on things other than passwords as well.
Hashing
"Used to map data of arbitrary (big) size,
to (non-informative) data of fixed (small) size."
To Illustrate, first something slightly dumber...
File Verification
Presumption: The network (or person) is imperfect. The bytes we receive may not always be the exact ones that were sent.
Also: The network or verification is "slow"
We need a shorter, but verifiable, version of the data.
Basic Checksumming
(technically the following is NOT checksumming)
Basic Checksumming
The grocery list:
Cheese
Crackers
Eggs
Ham
Koala
Mangoes
Salt
Underwear
Send the following...
Cheese
Ham
Eggs
Crackers
Koala
Salt
Underwear
Mangoes
CHECKSUM.45
CHECKSUM.45 = CHECKSUM.45
If the reciever gets
Cheese
Ham
Eggs
Crackers
Salt
Underwear
Mangoes
CHECKSUM.45
CHECSUM.40 = CHECKSUM.45? NO, SEND AGAIN.
Hashing
Error checking/Checksumming.
One tiny change in the original still means BIG changes in the gibberish.
(MD5, which is fast, but not super-secure) is good for this)
Verification:
Hashing Uses
Error Checking/Checksums
Password "Storage"
Bitcoin/Cryptocurrencies
Passwords
They don't store your password
(your secret ingredient)
They just store the entire milkshake....and calculate/mix it every time.
(don't use MD5, use something deliberately slow, like bcrypt)
To abuse some more analogies..
Consider your mom's _______ recipe?
(milkshake?)
Even if you don't know the ingredients..
... you know when it's WRONG :)
How passwords are done
Horrible - storing the password
Better but still bad - storing the password hashed
Decent - storing "userid+password" hashed
Best - storing "userid+password+salt" hashed
For example
Login: jmarks
password: g00dpassword
(salt): b00gab00ga (or better yet, change it every time)
jmarks+g00dpassword+b00gab00ga
==HASHED==>
02f39aae85ad73e162b446e918597e89
Sigh, passwords for humans
In the beginning, there was leetspeak
or should I say 1337sp34k.
n00b pr0n lololol
Hey, why did this happen in the first place? Not for passwords...
1337sp34k
Warning: Controversy ahead.
I'm following NIST, what they say makes A LOT OF SENSE to me:
You WILL see disagreement, feel free to form your own opinion
The Good Idea
Allow for, and perhaps require LENGTH.
That's IT.
Think passPHRASES, not words
The Good Idea
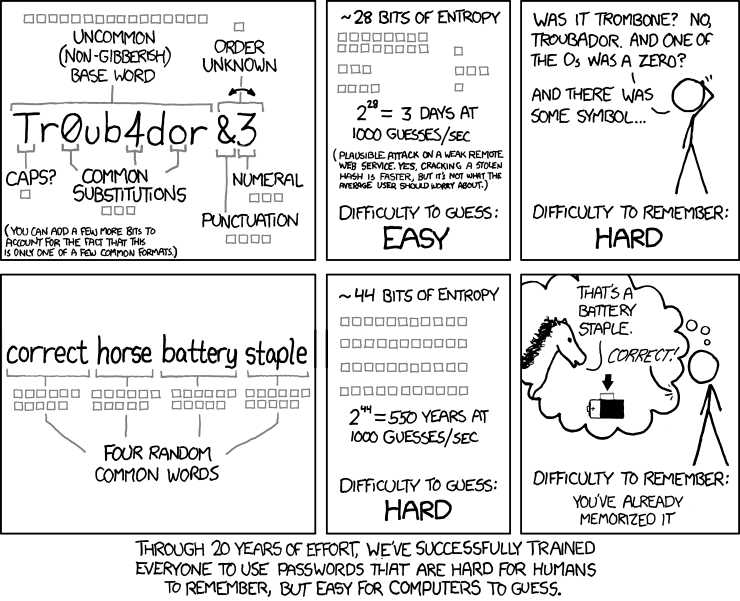
Bad ideas
Composition rules:
"At least one upper and one lowercase and a number.."
(We have a better solution, which is length)
Bad ideas
Password rotation - i.e. Change passwords every:
NAH, just pick a good one in the first place
Bad ideas
Password hints and Security Questions aka
Knowledge Based Authentication
ALWAYS LIE ON THESE. THEY ARE JUST SECONDARY PASSWORDS
https://www.mcsweeneys.net/articles/nihilistic-password-security-questions

Not NIST, but what I recommend
Make a good password
Write them down on paper and put in your wallet or purse. (Schneier agrees)
If you think you gangsta like I do
Remember the encryption thing you just did?
I write down my passwords in an encrypted text file. That's it.
Password Managers?
teach the controversy I guess.
They make NO SENSE to me, but clearly some find them acceptable.
2fa - Two Factor Authentication
Usually, a password and .. something else
Something else?
SMS?
Email?
Authenticator?
Hardware?
SMS
Not bad, but proving to be grimy, because cell phone companies aren't good at this..
Also not bad, but it's like the default backup for everything, so there you go.
Authenticators
e.g. Oauth. Pretty good. One time passwords, very similar to the "Bookstore Method"
PS, YEP, I STORE MY OAUTH KEYS in that same file and generate my 2fa #s from the command line. WHAT.
FIDO - Hardware
I mean, I suppose.
Other ideas, again:
(prof's opinion)
Biometrics are stupid*
Other ideas, again:
Biometrics are as stupid as Social security numbers
(i.e. decent USERNAMES or slight SECURITY THROUGH OBSCURITY)
I don't use 'em.
What else
Hey, so these hashes
They look like--
02f39aae85ad73e162b446e9
What are the odds that it would look like, say..
00000ae85ad73e162b446e9
Not IMPOSSIBLE, just VERY UNLIKELY.
A bit on banks and money
What is most money "made of?" How is it stored? Coins and little green pieces of paper?
A bit on banks and money
What is most money "made of?" How is it stored? Coins and little green pieces of paper?
NOPE.
Just (trusted) lists. Ledgers in banks and such.
Usually "digital"
In fact, lists are older than "money" itself.
Not dollars, but a list somewhere that says
"Ug owes Oof two cows"
"Oof owes Grok a stick"
or more accurately
"everybody owes the king taxes"
theorem: any system that involves writing down "ownership" and "what you've paid" for is (possibly) a bank = (gamestop, even)
But, you also might want "pieces/tokens"
GOLD AND DIAMONDS HA HA HA
(wait, seriously. Why are diamonds more expensive than water?)
Bitcoin and most other "Cryptocurrencies"
(note, some others don't work exactly this way)
A huge encoded/distributed online ledger/list, also called a "blockchain"
Powered/driven by "mining" (which is more like a slot machine, pull the lever, power the thing, and see if you "win")
Mining Bitcoin?
Randomly trying to find "nice looking" hashes.
......4E9BB99 nope.
.......000000 yep! $$$$
Mining
When you download a bitcoin (full node) wallet program, you literally have to get a copy of every single transaction ever.
Transactions are computationally expensive.
The "Mining" also powers the "hashed transactions..eg."
02b23 gave bf239 .005 bitcoins. I can prove it because the hash of this transaction is =>
081ee23
Add this to the chain and spread it around.
Bitcoin transaction.
You "add your new or old hash movement" to the ledger. By making another special hash. Which is "expensive."
This work powers the blockchain and "proves" that you've put in work. By design, the system "rewards" you for it.
Bitcoin transaction.
Now, why is it valuable?
Because people believe it is.
See also: gold, beanie babies, crappy companies, virtual swords, pokemon cards, sneakers, whatevs.
Bitcoin transaction.
PS: Crypto addresses? Just numbers in different bases (sometimes with a prefix):
Functionally similar to public keys
BTC: 18L1qxHaN1i8ihrLMX8sxrQLmfoaTWud9R
ETH: 0xD54b6C55A8aEc0bec04Cb6b3eB6F84F6BcF03619
(these are 100% real, please feel free to send me money :) )
"Blockchain"
It's a large public database, in which everyone can see every transaction. That's all.
Now give me a bunch of money because I just said "blockchain" :)
Backlinks: FSU Courses:LIS4774:RawSlides