Week 9 - Pre Networking
Created Wednesday 21 October 2020
Layers (OSI)
Application (HTTP, telnet, etc)
Presentation (framework MIME)
Session (pipe,SOCKS)
Transport (reliable packet delivery, TCP or UDP)
Network (nodes and address, IP)
Data (PPP)
Physical (wires, radio, USB)
Please Do Not Throw Sausage Pizza Away
Layers (OSI)
Application (HTTP, telnet, etc)
Presentation (framework MIME)
Session (pipe,SOCKS)
Transport (reliable packet delivery, TCP or UDP)
Network (nodes and address, IP)
Data (PPP)
Physical (wires, radio, USB)
NOTE - NEARLY EVERYTHING ABOVE PHYSICAL CAN
GET ALL JUMBLY AND SWITCHED AROUND
There is no cloud.
The Internet:
A bunch of computers connected together, that's it.
The ones in the middle do routing and transfer
IP addresses
Because numbers can be big, we could have a system that simply assigns
a unique number to every computer connected to the internet.
In fact we do, it's called IPv6
IP addresses
Because numbers can be big, we could have a system that simply assigns
a unique number to every computer connected to the internet.
In fact we do, it's called IPv6
(lOl wE DonT eveN UsE iT rEALly..
working on it, but we're still at about 94% the other thing
IP Addresses (IPv4)
4 billion oughta be enough, right? nooope, so we need NAT
Network
Address
Translation
This is what the ROUTERS do
if you see:
192.168.*.*
10.*.*.*
etc, these are "internal" networks. The routers do the job of subdividing
Internal networks
These can be deeply physical- pure wire

They can be wireless. Probably what you got at your house

And they can be virtual. VPN
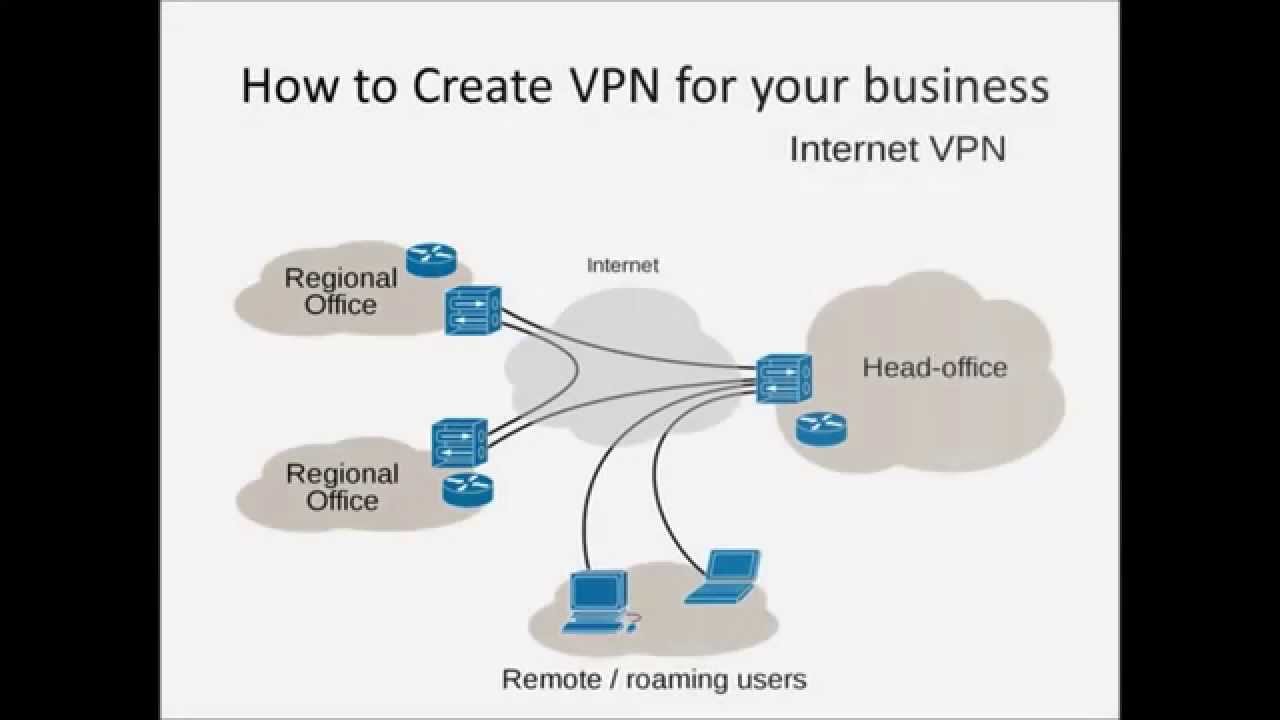
What is a VPN again?
Badly named, of course:
//TECHNICALLY://
A Virtual Private Network
THE THING YOU SEE ADVERTISED
Uses VPN technology to act as a
QUASI-ANONYMOUS ENCRYPTED PROXY
So you could have a use/need for multiple VPNS
(and crappy Android only lets you have one, jerks, whats the deal with apple?)
- To connect to your other devices securely (e.g. OpenVPN, Tinc, Wireguard)
- To wall off a network in some way (e.g. our SecNet, company / FSU vpns)
- To browse the net without your ISP or company knowing (but your VPN can)
- To do some low level ad/crap blocking, e.g. housewide (DNS66, PiHole)
(and you can mix up all these. I kind of know how and kind of don't)
One thing the above does: it mixes up the layers
TCP/IP AGAIN! (Your "new" VPN address)
-VPN (e.g. OpenVPN)
TCP (or UDP)/IP (with your "real" ip address / or router address)
(note, all are usually still valid by default unless your routing says otherwise)
TCP vs UDP
TCP - reliable handshake where you verify packets (SYN/ACK)
(important for encryption et al. VERIFICATION)
UDP - just spray them datas out there and see what happens
(cool for things like streaming, where the reassembly is heavy work by the computers)
TCP vs UDP
Tasteful Consensual Photos
(Hello, may I send you this?
Yes you may.
Here you go!
Thank you!)
TCP vs UDP
Unsolicited D(ramatic?) Pics
JUST BLASTIN PACKETS OUT THERE
SSH - another tool to do this sort of thing
SSH is a tool for directly (like by typing commands as if you were in front)
and INDIRECTLY (forwarding ports and services)
ssh -N -L 1993:outlook.office365.com:993
-L 1587:smtp.office365.com:587 pi@fib0
(real talk if you seriously need this holler at me)
PORTS
Somewhat like "telephone extensions" —
Or perhaps "doors vs. windows. vs garage doors vs. cargo doors, etc"
Further subdivides computer/IP addresses for purposes of separating concerns
e.g. We expect WEB traffic on 80 or 445 (though we can use a different one,
this is like climbing through a window even though there is a door)
PORTS
e.g.:
22 - SSH
80 - unencrypted Web
445 - encrypted Web
6881-6889 - Bittorrent
More on Ports
The CLASSICS:
21 - FTP
23 - Telnet
25 - SMTP (unencrypted)
53 - DNS (you shouldn't have this open)
90 - http (unencrypted)
110- POP
143 - IMAP (unencrypted)
3389 - RDP
Once again, a simple explanation of why Microsoft deserves to be bankrupt:
What's a good and easy way to secure a building? (assume locks work)
One way would be to lock all the doors and windows, and then only open the ones you need when you need to?
Reasonable and linuxy
Or you could do what Windows did

Once again
The reason for this mess.
A computer doesn't do anything unless it is told to.
The Windows people wrote the software this way:
- Ports open
- With programs listening and willing to obey orders
- that could **** up your system.
Linux doesn't do this
And when it does, it's a mistake, not a design choice.
You have to MANUALLY turn on the programs that listen and obey orders.
(e.g. SSH or a web server, etc. Usually not the Microsoft backdoors, et al
but you know, those updates)
Cybersecurity words:
Open ports are now part of your "attack surface"
And you need to minimize that.
UPNP
Universal Plug 'n Play
Basically, the opposite of a firewall. Opens your router ports automatically
ROUTING:
Gateways, Addresses and Masks, oh my.
Routing works via Masks; i.e. if the first set of numbers matches a rule, you route that way..
If not, you go down the chain until something does, or you hit a default
ALSO OTHER STUFF
Hostnames
Locally, you can mostly pick your own.
Also, you may choose within a domain
DNS (Domain Name System)
Turns e.g. jrm4.com to 75.73.272.28
(hehe why is this fake for sure?)
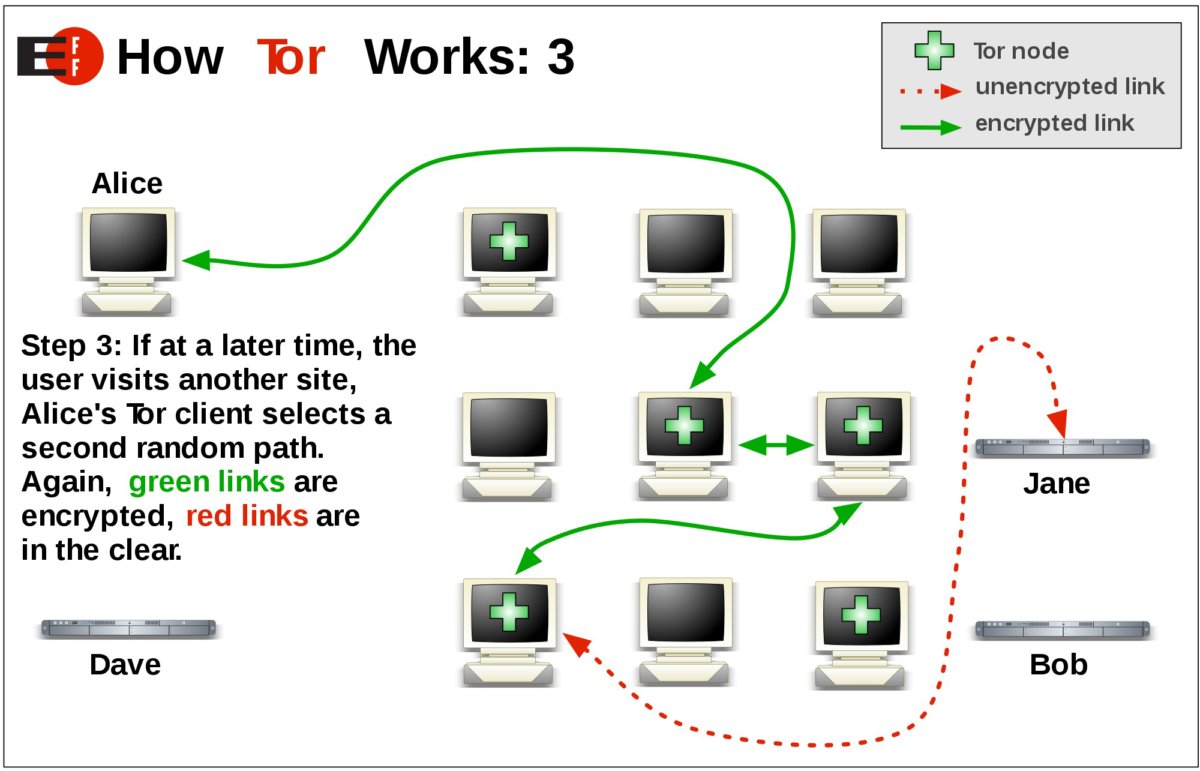
Other Tools: TOR
TINC vpn
SSH
Default port 22
But, as mentioned last time, you *could* change it.
Some places will not allow you to.
This is a common attack surface, for obvious reasons —
This is the default method for "being in front" of a computer remotely.
(as mentioned before, you can also tunnel through here)
Backlinks: FSU Courses:LIS4774:RawSlides